Nowadays, the increase in the number of security incidents experienced by systems and their impact on the business has become a major concern.
If the necessary precautions are not taken, any system handling sensitive or confidential information is at risk of being attacked and breached.
Every day, new ways to attack a system emerge. It therefore becomes crucial to be up-to-date in terms of security, and that task must be part of the development and maintenance stages of any software.
1. Complex Attack Surfaces
Modern applications often have complex attack surfaces with various entry points, making it challenging to identify all potential vulnerabilities.
2. Continuous Evolving Threat Landscape
The threat landscape is constantly evolving, and new security threats emerge regularly.
3. Authentication and Authorization Testing
Ensuring robust authentication and authorization mechanisms can be challenging, especially in applications with complex user roles and permissions.
4. Data Privacy Concerns
Protecting sensitive user data is a critical aspect of security testing, and compliance with data protection regulations is essential.
5. Third-Party Integration Risks
Integrating with third-party services or libraries introduces potential security risks.
6. Client-Side Security
Securing the client-side of web applications can be challenging, especially with the prevalence of client-side scripting and complex user interfaces.
7. Secure Configuration Management
Misconfigurations in application servers, databases, and other components can introduce security vulnerabilities.
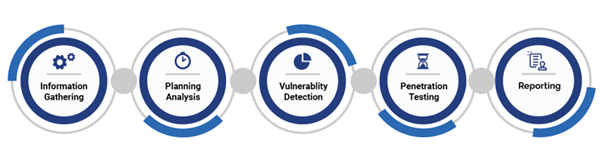
Using an approach based on security tests, it is possible to identify vulnerabilities within a system and understand whether that system is protected against different types of attacks.
Penetration tests are a way to evaluate security from an attacker’s point of view, whether the attacker is external or within the organization itself. There are other ways to address security matters, such as analyzing the source code, integrating verification and validation activities during the software’s lifecycle.
We have a team of specialists capable of evaluating the security of your systems, with industry-recognized certifications such as Burp suite.
How We Work With You :The pandemic prompted many companies to incorporate specialized security checks such as risk assessments, security measures, vulnerability scans, security audits, security scanning, and API security into their infrastructure. Softdevels aims to identify security threats and offer suggestions for their eradication. With over 5+ years of experience, we provide end-to-end security services that include vulnerability management, risk assessments, posture assessment, and much more to help improve security posture.
Technical Details
Methodology and International Standards :The methodology applied to security services is based on techniques, tools and processes proposed by the OWASP international organization.
OWASP’s Top 10 is one of the most important vulnerability rankings across the world, and is used as a guide to prioritize and create awareness.
Other standards such as the OWASP Testing Guide, the OWASP Application Security Verification Standard (ASVS) and the OWASP Mobile Application Security Verification Standard (MASVS) are used to evaluate different solution types.
Depending on the activities or the industry for each organization, the practices suggested by international standards are also applied. These include, for example, ISO 27.000, HIPAA, GDPR and PCI-DSS, among others.
Penetration Testing : Conduct regular penetration testing to simulate real-world attacks and identify vulnerabilities that automated tools might miss.
Security Training and Awareness : Provide security training for development and testing teams to ensure a solid understanding of security best practices and potential threats.
Code Reviews : Integrate security reviews into the code review process to identify and address security issues early in the development lifecycle.
Incident Response Planning : Develop and regularly update an incident response plan to efficiently handle security incidents and minimize the impact of breaches.
Compliance Testing : Ensure that security testing aligns with industry-specific compliance standards and regulations relevant to the application and organization.
Security Automation : Implement security testing automation where possible, such as automated security scanning and continuous integration security checks, to identify and address vulnerabilities quickly.
Bug Bounty Programs : Consider implementing bug bounty programs to leverage the collective expertise of the security community in identifying and responsibly disclosing vulnerabilities.
By addressing these challenges and incorporating best practices, organizations can establish a robust security testing strategy that helps identify and mitigate potential security risks in their software applications.